Today’s malware-loader-du-jour, Bumblebee, has been seen achieving initial access through phishing sites that convince a user to mount a downloaded ISO image. This may be a reaction to Microsoft’s recent improvements to macro-enabled document security.
Adversaries push ISO files through compromised email (reply) chains, known as thread hijacked emails, to deploy the Bumblebee loader. ISO files contain a byte-to-byte copy of low-level data stored on a disk. The malicious ISO files are delivered through Google Cloud links or password protected zip folders. The ISO files contain a hidden DLL with random names and an LNK file. DLL (Dynamic Link Library) is a library that contains codes and data which can be used by more than one program at a time. LNK is a filename extension in Microsoft Windows for shortcuts to local files.
https://cloudsek.com/technical-analysis-of-bumblebee-malware-loader/
One of the things that we can do to help our users avoid this new initial execution foothold is by blocking the mounting of ISO images, as long as you can be confident this will not break anything they actually need to do! I am fortunate enough to be able to do this.
(Djordje Atlialp shows us how to achieve this with classic GPOs, and also a more comprehensive neutering of ISO files.)
Here is what I have rolled out as an Intune PowerShell Script to block the mounting of ISOs. No reboot is required. Users will see the Mount option disappear from the context menu of an ISO file within File Explorer and will be unable to double-click to mount a malicious ISO. Or, indeed, any ISO. 😉
We will head to Microsoft Endpoint Manager admin center, go to Devices > Scripts and create a new Windows 10 and later PowerShell script.
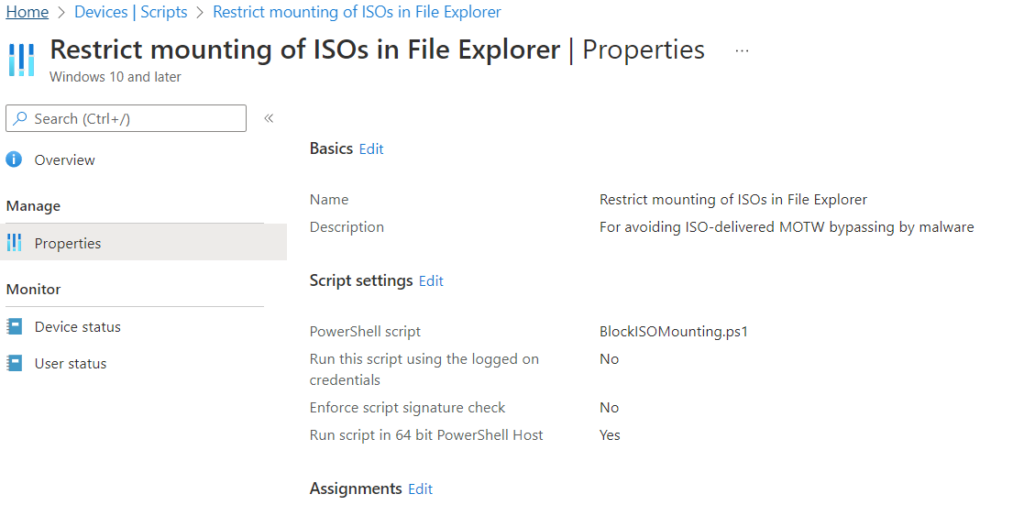
The Intune Script
UPDATE: I have made some improvements — namely, the previous one liner will cause failures to be reported in Intune on subsequent runs. We will now only add the value where it does not exist, and we will add support for Windows.VhdFile as well. It’s no longer a one-liner!
$items = @(
@{
path = "HKLM:\SOFTWARE\Classes\Windows.IsoFile\shell\mount"
valueName = "ProgrammaticAccessOnly"
}
@{
path = "HKLM:\SOFTWARE\Classes\Windows.VhdFile\shell\mount"
valueName = "ProgrammaticAccessOnly"
}
)
foreach($item in $items) {
if ($null -eq (Get-Item -Path $item.path).GetValue($item.valueName)) {
New-ItemProperty -Path $item.path -Name $item.valueName -Value ""
}
}The body of the script can be as follows:
New-ItemProperty -Path "HKLM:\SOFTWARE\Classes\Windows.IsoFile\shell\mount" -Name ProgrammaticAccessOnly -Value ""(This REG_SZ value need only exist, with a blank string as its Data, for this to work.)
Assign it to the device group and you are all set.
Removal
To undo this change, we can reverse what we’re doing and Remove-ItemProperty on the items we added:
$items = @(
@{
path = "HKLM:\SOFTWARE\Classes\Windows.IsoFile\shell\mount"
valueName = "ProgrammaticAccessOnly"
}
@{
path = "HKLM:\SOFTWARE\Classes\Windows.VhdFile\shell\mount"
valueName = "ProgrammaticAccessOnly"
}
)
foreach($item in $items) {
if ($null -ne (Get-Item -Path $item.path).GetValue($item.valueName)) {
Remove-ItemProperty -Path $item.path -Name $item.valueName
}
}Conclusion
This doesn’t make you bulletproof, but will, if tolerated by your users, provide a substantial degree of protection, at the time of writing, from any number of current malware loaders that are using the ISO image technique to achieve initial code execution. The nature of the separate filesystem within the ISO presently prevents it from being marked as being from the Wild Wild West World Wide Web.